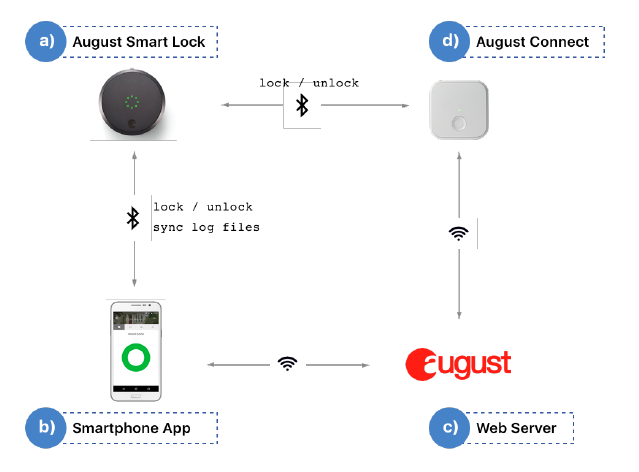
Your August Smart Lock should grant convenience—not become a backdoor for intruders. Yet security researchers have exposed critical flaws where attackers could steal your Wi-Fi password or grant themselves permanent access to your home. While no physical break-ins have been documented through these vulnerabilities, the risks are real and demand immediate action. If you own an August Smart Lock Pro with Connect Bridge or granted guest access before August 2020, your system may still be exposed.
This guide cuts through the technical jargon to reveal exactly how hackers exploit August Smart Locks, which models are vulnerable, and the 10-minute security checklist that locks down your home. You’ll learn why updating firmware isn’t enough—and why your Wi-Fi password might already be compromised if you set up your Connect Bridge before 2020.
Stealing Your Wi-Fi Password During Setup
.png)
How Hackers Intercept Your Network Credentials
When configuring your August Connect Bridge for the first time, your Android device transmits your home Wi-Fi password through a critical flaw researchers call CVE-2019-17098. During setup, the Connect Bridge creates an open temporary network. Your Android phone connects to it and sends your actual Wi-Fi credentials—but the encryption protecting this data uses a static key hardcoded into the app. Worse, August protected this key with a ROT-13 cipher, a basic substitution method easily cracked by anyone with minimal technical skills.
What happens in a real attack: A hacker within 30 meters uses a Wi-Fi sniffer to capture setup traffic. They decode the ROT-13 obfuscation, apply the static AES key, and instantly obtain your Wi-Fi password in plain text. This isn’t theoretical—Bitdefender’s team demonstrated it in lab tests, showing how attackers could even trick you into reconfiguring your lock to trigger the vulnerability.
Is Your August Lock Vulnerable to Wi-Fi Theft?
At immediate risk:
– August Smart Lock Pro (Gen 2) paired with Connect Bridge
– Any lock configured using the Android app before August 2020
– Systems where someone forced a re-setup (e.g., phishing scam)
You’re safe if:
– You use the August Wi-Fi Smart Lock (2020 model with built-in Wi-Fi)
– You rely solely on Bluetooth without Connect Bridge
– You’ve only ever used iOS for setup (Apple’s security blocks this flaw)
Patch Your Lock Against Wi-Fi Credential Theft
August rolled out fixes in August 2020, but you must manually verify your protection:
1. Open the August app → Settings → Device Info → Check for Updates
2. Confirm Connect Bridge firmware is v2.2.14 or newer
3. Update your Android app to v3.4.2+ via Google Play Store
4. Change your Wi-Fi password immediately if Connect was set up before August 2020
Critical note: Even with patches, if your Wi-Fi password was exposed during initial setup, attackers could still access your network. Treat this as a potential breach until you rotate passwords.
Former Guests Unlocking Your Door Indefinitely
The Secret Key Conversion Attack
At DEF CON 28, researcher Jmaxxz revealed a terrifying flaw: guests you revoke can keep permanent access. When you invite someone through the August app, they receive an encrypted digital key. The vulnerability let guests modify this key’s metadata on their device—converting a temporary guest pass into an owner-level key. Crucially, this forged key kept working even after you removed their access in the app.
Real-world danger: A former house cleaner, Airbnb guest, or disgruntled roommate could silently retain entry privileges. Researchers proved this works with 100% success on unpatched locks using jailbroken iPhones and Frida hacking tools. Imagine believing you’ve revoked access—only for that person to walk in months later.
How August Fixed the Guest Key Loophole
August deployed two critical layers of defense:
– Server-side patch (August 19, 2020): Blocks privilege escalation attempts by validating key permissions on their cloud servers
– Firmware update v2.1.8 (August 24, 2020): Prevents local modification of key files on the lock itself
To stay protected:
– Confirm your lock firmware is v2.1.8 or newer in the app
– Never skip guest list reviews—audit permissions monthly
– Use one-time access codes instead of app-based keys for contractors
Bluetooth Hacks: Industry Weaknesses vs. August’s Defenses
Common Bluetooth Attack Methods
While August implemented stronger safeguards than many competitors, Bluetooth-based locks face inherent risks:
– Replay attacks: Hackers record and rebroadcast unlock signals using tools like Ubertooth One
– Extended-range intrusions: Directional antennas can intercept signals up to 50 meters away
– Weak pairing: Older locks using “Just Works” Bluetooth pairing lack encryption verification
August-specific protections:
– All lock commands use AES-128 encryption
– Firmware updates require RSA 2048-bit digital signatures
– Pairing demands August app authentication—blocking rogue device connections
Important: These defenses only work if you keep firmware updated. Unpatched locks remain vulnerable to credential-sniffing attacks.
Your 10-Minute August Lock Security Checklist
Critical Updates You Must Verify Now
- Check firmware versions:
– Open August app → Settings → Device Info
– Lock firmware must be v2.1.8+
– Connect Bridge firmware must be v2.2.14+ - Update your Android app (iOS users: ensure app is current)
- Rotate your Wi-Fi password if Connect was set up pre-August 2020
Lock Down Guest Access Permanently
- Switch to temporary codes: In the app, generate one-time 6-digit codes for visitors instead of app-based keys
- Enable two-factor authentication for your August account (Settings → Security)
- Delete unused guests immediately—don’t just “revoke” access
- Set monthly reminders to audit your guest list
Fortify Your Network Security
- Create a dedicated IoT network: Isolate smart locks on a guest Wi-Fi VLAN
- Monitor router logs for unknown devices after setup sessions
- Use iOS for future configurations—immune to the Wi-Fi password theft flaw
- Disable WPS on your router (a common attack vector for IoT devices)
Don’t Forget Physical Security Basics
Your August Smart Lock is only as strong as your door’s construction. Maintain these non-negotiables:
– Test manual key operation every 90 days—lubricate the keyway annually
– Reinforce the strike plate with 3-inch screws into the door frame
– Store backup keys with a trusted neighbor—not under a mat
– Check door alignment monthly; gaps wider than 1/8 inch enable forced entry
August’s Security Track Record: What to Watch
Transparency Concerns After Vulnerability Reports
August’s response to researchers raises red flags:
– Initial contact: Responded in 8 days (good)
– Patch development: Took 240 days from disclosure to fix (unacceptable)
– Public statements: Downplayed risks—calling guest key exploits “hacking your own phone”
Ongoing Vigilance Required
- Check for firmware updates monthly—don’t wait for prompts
- Subscribe to August’s security newsletter for patch announcements
- Verify third-party audits—none published since 2020 patches
- Join security forums like r/homeautomation for community threat reports
Bottom Line: Your August Lock Is Safe—If You Act Now
The August smart lock hack vulnerabilities are patched, but your security depends entirely on your actions. If you’ve updated firmware and apps since August 2020 and rotated your Wi-Fi password, your system is secure against known exploits. However, complacency is your biggest enemy—smart locks require the same maintenance as physical locks.
Take these steps today:
1. Verify firmware versions in your August app
2. Replace Wi-Fi passwords if Connect was set up pre-2020
3. Switch to one-time guest codes instead of app-based keys
Treat your digital keys like physical ones: rotate access regularly, monitor usage, and never assume “set it and forget it” security. Schedule quarterly lock maintenance alongside changing smoke alarm batteries—because the most sophisticated smart lock won’t stop a compromised network or outdated firmware. Your home’s safety isn’t just about hacking headlines; it’s built on consistent, simple habits that keep intruders outside where they belong.